Critical Threat Intelligence & Advisory Summaries
Threat Intelligence Brief: North Korean IT Worker Scheme Highlights AI-Enabled Insider Access Risk
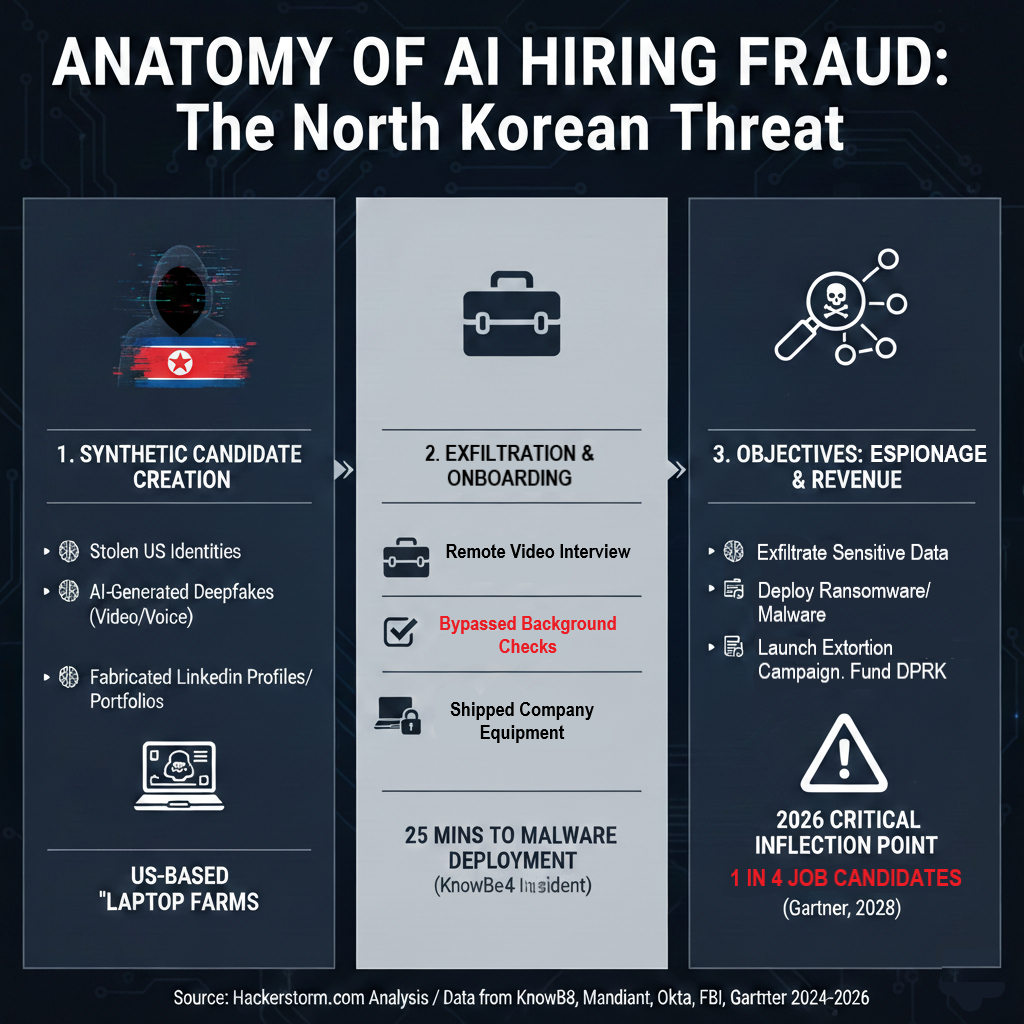
Summary: KnowBe4 detected a suspected North Korean IT worker within 25 minutes of onboarding, exposing operational risks from AI-generated resumes, deepfake interviews, and synthetic identities. Security teams should focus on onboarding monitoring, least-privilege access, and early behavioral detection to prevent persistent insider threats.
A July 2024 incident involving cybersecurity firm KnowBe4 is being cited by security leaders as a growing operational risk: threat actors using synthetic identities, generative AI, and remote hiring processes to obtain legitimate enterprise access.
The case illustrates how AI-enabled hiring fraud is evolving from a financial or HR concern into a potential insider threat vector, with implications for access control, onboarding security, and early-stage monitoring.
Incident Summary
KnowBe4 disclosed that it detected and contained a suspected North Korean–linked IT worker within 25 minutes of initial system access after the individual received corporate equipment.
According to the company:
- The candidate completed multiple video interviews
- Background checks and reference verification were passed
- A stolen U.S. identity was used
- Suspicious activity was detected shortly after login
The device was isolated before significant damage occurred. The company later reported continued application attempts believed to be linked to North Korean remote IT worker networks.
The incident demonstrates that traditional hiring validation methods — including live video interviews and identity checks — may be insufficient against AI-enhanced impersonation.
Threat Context: North Korean Remote IT Worker Operations
U.S. federal agencies, including the FBI and Department of Justice, have issued multiple advisories describing coordinated efforts by North Korean nationals to obtain remote technology roles using stolen or synthetic identities.
Reported characteristics include:
- Fabricated LinkedIn profiles and portfolios
- Use of U.S.-based “laptop farms” to simulate local presence
- VPN and proxy infrastructure
- Multiple simultaneous remote roles
- Revenue routed back to support state operations
Threat intelligence reporting from Mandiant, CrowdStrike, Okta, and Google Threat Intelligence Group indicates the activity has expanded beyond U.S. technology companies to include financial services, healthcare, professional services, and public sector organizations.
Similar targeting has been observed in the United Kingdom and Europe.
How Generative AI Enables Hiring Fraud
Advances in generative AI are reducing the effort required to create convincing synthetic job candidates.
Security researchers report that threat actors can now:
- Generate tailored resumes and work histories
- Conduct real-time deepfake video interviews
- Clone voices using minimal audio samples
- Modify facial appearance, language, or accent
- Maintain multiple remote roles using automation
Industry analysis cited in threat intelligence reporting suggests that a growing percentage of job candidate profiles may be partially or fully synthetic by the end of the decade.
For security teams, the primary risk is not the hiring event itself — but the legitimate credentials and system access granted afterward.
Security Impact Analysis (Hackerstorm)
Attack Vector
Valid account access obtained through employment (MITRE ATT&CK: T1078 – Valid Accounts)
Primary Risk
Persistent insider access enabling:
- Data exfiltration
- Intellectual property theft
- Malware deployment
- Extortion or ransomware staging
- Long-term espionage
Exposure Window
Highest risk period occurs during:
- Initial onboarding
- Early privilege expansion
- Remote equipment provisioning
Detection Opportunity
Behavioral anomalies typically appear within the first hours or days of access, particularly where least-privilege controls are enforced.
Why Traditional Hiring Controls Are Failing
The KnowBe4 case highlights structural gaps in many organizations’ onboarding security:
- Identity verification designed for pre-AI threat models
- Overreliance on video interviews as proof of identity
- Limited SOC visibility into new hires
- Immediate access to production environments
- Lack of behavioral monitoring during probation periods
As generative AI improves, visual and voice verification alone should no longer be considered high-confidence identity controls.
Detection Focus for Security Operations
Security teams should monitor newly onboarded users for:
- Rapid privilege escalation attempts
- Access outside assigned role scope
- Unusual data access or download patterns
- Use of unauthorized remote access tools
- Logins from unexpected network locations
- Attempts to disable endpoint protections
Early SOC involvement in onboarding significantly reduces dwell time.
Control Priorities for Enterprises
Security leaders increasingly recommend treating recruitment and onboarding as part of the enterprise attack surface.
Immediate Controls
- Least-privilege access for all new employees
- Enhanced endpoint monitoring during the first 30–90 days
- Out-of-band identity verification (secondary validation channels)
- Cross-validation of banking, payroll, and identity data
- Dual authorization for high-risk financial or administrative actions
Strategic Controls
- HR–Security integration for high-risk roles
- Behavioral analytics for new accounts
- Device and location consistency checks
- Formal insider risk monitoring programs
Organizations with mature onboarding monitoring are significantly more likely to detect anomalous activity early.
Broader Trend: Insider-as-a-Service
Threat intelligence reporting indicates that some North Korean IT workers have used legitimate employment access to support:
- Corporate espionage
- Data theft operations
- Malware deployment
- Extortion campaigns
Security analysts increasingly describe this model as “insider-as-a-service,” where attackers bypass perimeter defenses by entering through legitimate hiring channels.
Separately, law enforcement and industry reports have documented multiple cases of AI-enabled deepfake impersonation used in financial fraud and executive impersonation schemes, reinforcing the growing reliability of synthetic identity attacks.
Risk Outlook for 2026
Fraud and threat intelligence forecasts indicate:
- Increasing use of automation and AI to scale identity-based attacks
- Continued growth in global remote hiring
- Expansion of synthetic identity use across multiple fraud categories
For most organizations, the operational question is no longer whether AI-enabled hiring fraud will occur, but whether anomalous behavior can be detected before persistent access is established.
Who Is Most at Risk
Highest exposure sectors include:
- Technology and software development
- Managed service providers (MSPs)
- Financial services
- Healthcare and life sciences
- Professional and consulting services
- Government contractors and public sector organizations
Any organization providing remote system access to newly hired technical staff should treat onboarding as a high-risk security phase.
Key Takeaway
AI-enabled hiring fraud should be treated as a credential-based intrusion vector, not an HR anomaly.
The most effective defenses focus on:
- Early behavioral detection
- Strict least-privilege access
- Integrated HR and security workflows
- Monitoring during the initial access window
In the current threat landscape, the onboarding process represents a growing and often overlooked entry point for advanced threat actors.
About This Report
Reading Time: Approximately 15 minutes
This Threat Intelligence Brief is based on publicly disclosed corporate incident reports, U.S. law enforcement advisories, federal court records, and threat intelligence research from multiple cybersecurity organizations.
Information reflects the operational threat landscape as of February 2026.
Author Information
Timur Mehmet | Founder & Lead Editor
Timur is a veteran Information Security professional with a career spanning over three decades. Since the 1990s, he has led security initiatives across high-stakes sectors, including Finance, Telecommunications, Media, and Energy. Professional qualifications over the years have included CISSP, ISO27000 Auditor, ITIL and technologies such as Networking, Operating Systems, PKI, Firewalls. For more information including independent citations and credentials, visit our About page.
Contact:
Editorial Standards
This article adheres to Hackerstorm.com's commitment to accuracy, independence, and transparency:
- Fact-Checking: All statistics and claims are verified against primary sources and authoritative reports
- Source Transparency: Original research sources and citations are provided in the References section below
- No Conflicts of Interest: This analysis is independent and not sponsored by any vendor or organization
- Corrections Policy: We correct errors promptly and transparently. Report inaccuracies to
This email address is being protected from spambots. You need JavaScript enabled to view it.
Editorial Policy: Ethics, Non-Bias, Fact Checking and Corrections
Learn More: About Hackerstorm.com | FAQs
